Cybersecurity in healthcare is not optional; it's essential. Healthcare cyberattacks surged by 55% in 2023, a stark reminder that patient care now depends as much on secure networks as it does on skilled clinicians. And because October is Cybersecurity Awareness Month, it's the perfect moment to double down on protecting the systems, data, and people that keep care moving.
For mobile medical services, the risks are uniquely complex. Teams work across varied locations and networks, connect to client systems, and often use mobile devices to document care in real time. That mobility enables access, but it also expands vulnerabilities in ways traditional healthcare settings don't always face.
In this blog, we'll explore why healthcare is such a high-value target and what's truly at stake, from patient safety to organizational reputation.
The High Stakes of Cybersecurity in Healthcare
When we talk about digital security, we're also safeguarding lives and trust. The importance of cybersecurity in healthcare is magnified because our industry is, unfortunately, a prime target for cybercriminals.
Medical Records
Unlike a credit card that can be canceled and reissued, a full electronic health record (EHR) contains a lifetime of data: Social Security numbers, addresses, and financial details.
This makes them extremely valuable for identity theft and medical fraud. In fact, a complete medical record is worth up to 10 times more than credit card data on the dark web.
Critical Infrastructure
More than just an inconvenience, a cyberattack can force a practice to shut down, divert ambulances, or prevent physicians from accessing necessary patient information. Criminals know this, and it makes them more likely to attempt a ransom payment.
Security Systems
Many organizations lag behind other industries in IT investment. Relying on outdated security systems or neglecting regular patching leaves wide-open doorways for sophisticated attacks like ransomware.
Patient Safety Risks
When systems are locked down by ransomware, service providers could lose access to charts, prescription history, lab results, and even medical device controls. A system outage may even delay treatment, leading to medication errors and resulting in poor patient outcomes.
Financial Costs
Healthcare has consistently reported the highest average cost of a data breach of any industry for 13 years running. The average cost of a single healthcare breach has recently soared to $10.93 million, encompassing everything from legal fees to regulatory fines.
Reputation Damage and Loss of Patient Trust
For an occupational health provider, trust is everything. A breach doesn't just cost money; it damages the faith that clients and individual patients place in keeping their most personal information private. This reputation damage can lead to a long-term loss of patient volume that is difficult to recover from.
HIPAA Compliance and PHI Protection

The importance of cybersecurity in healthcare is underscored by the Health Insurance Portability and Accountability Act (HIPAA), which establishes standards for protecting patient data. Such data is commonly referred to as Protected Health Information (PHI).
The core of data security lies in the HIPAA Security Rule, which requires 3 essential categories of safeguards for all electronic PHI (ePHI).
HIPAA Security Rule Requirements
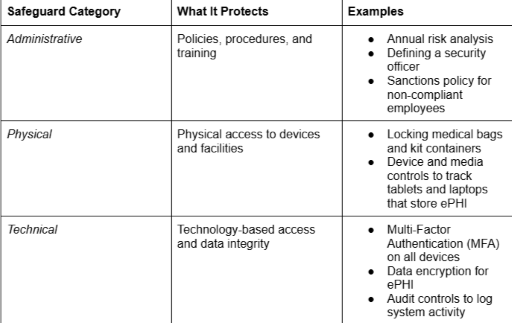
PHI in Mobile Medical Settings
The unique nature of mobile and occupational health services means PHI is constantly on the move, increasing the risk profile. In our daily operations, PHI includes:
- Electronic Health Records on Mobile Devices: Clinical notes, treatment plans, and past medical history accessed via encrypted laptops or tablets.
- Biometric Data from Health Screenings: Information gathered during on-site services, such as lab results, hearing tests, and drug screening results.
- Employee Health Information: Confidential data specific to employee injury reports, disability claims, or return-to-work clearances, which must be stored separately from general personnel files.
Penalties for Non-Compliance
HIPAA violations carry severe, escalating penalties enforced by the Health and Human Services (HHS) Office for Civil Rights (OCR).
- Financial Costs/Civil Penalties: Fines are categorized into tiers based on culpability (from "Did not know" to "Willful Neglect") and range from $141 up to $71,162 per violation, with an annual cap exceeding $2 million. Even minor, accidental breaches can result in significant fines if a proper risk analysis wasn't completed.
- Potential Criminal Charges: In cases of knowingly obtaining or disclosing PHI for personal gain or malicious harm, individuals can face up to 10 years in prison and fines of up to $250,000.
- Business Reputation Consequences: The HHS is required to publish details of large breaches. This permanent record of a security failure can lead to an immediate, catastrophic loss of trust.
Cybersecurity Issues for Healthcare in Mobile Medical Services
For occupational health practices that rely on mobility, the foundational HIPAA rules face a set of obstacles. The very nature of operating outside of a traditional, secure clinical environment significantly expands the attack surface.
Mobile Workforce Vulnerabilities
Unsecured Wi-Fi Networks at Client Sites
When staff conduct on-site screenings, connecting to a client's network or public Wi-Fi exposes sensitive ePHI to interception. These networks often lack the necessary encryption or network segmentation to safely transmit patient data.
Lost or Stolen Devices Containing PHI
A laptop, tablet, or smartphone lost in transit or stolen from a vehicle is a major HIPAA breach waiting to happen. Without mandatory device encryption and remote-wipe capabilities, the loss of the physical device immediately becomes a massive data breach.
Bring Your Own Device (BYOD) Policies
While allowing employees to use their personal phones or tablets can be efficient, it blurs the line between personal security and patient data security.
Without strict Mobile Device Management (MDM) software, personal apps, downloads, and web use could easily introduce malware or create backdoors to your organization's systems.
Third-Party Integrations
Client System Connections
Occupational health often means integrating results directly with a client's Human Resources or safety management system. Each connection requires careful vetting and a signed Business Associate Agreement (BAA) to ensure clients are protecting the PHI shared.
Cloud-Based EMR Systems
Cloud-hosted electronic medical records (EMRs) allow for efficient access. While convenient, the security of this system is heavily dependent on security protocols and strong access controls.
Medical Device Connectivity
Diagnostic tools used in mobile units (i.e., audiometers or spirometers) are increasingly connected to a network to transmit data. These Internet of Medical Things (IoMT) devices are often built without strong security features, offering hackers another point of entry into the system.
Resource Constraints
Limited IT Budgets
Investing in sophisticated security tools, 24/7 monitoring, and dedicated security personnel is challenging when operating on a tight budget. As a result, many practices are forced to rely on basic, often inadequate security measures.
Lack of Cybersecurity Staff
Most occupational health practices rely on a single IT person or a general office manager to handle security, a task that requires specialized, full-time expertise. A lack of dedicated expertise means risk assessments, patching, and incident response planning are often neglected.
Balancing Security with Efficiency
Every security measure (i.e., a complex encryption process) adds a step and costs time. The constant struggle is to find the perfect balance that keeps data secure without crippling the speed required to deliver timely, on-site patient care.
Emerging Cybersecurity Threats in Healthcare

The threats facing occupational health are not static. Rather, they are rapidly evolving, driven by the increasing professionalization and AI-powered tactics of cybercriminals. Staying secure requires understanding what the next generation of attacks looks like.
Ransomware Attacks
Ransomware remains the top concern, but the methodology is becoming more targeted.
- Healthcare-Specific Ransomware Variants: Threat actors are now creating ransomware-as-a-service (RaaS) variants. This ransomware type is explicitly designed to maximize impact within healthcare environments, targeting critical systems like EMR and patient scheduling.
- Double Extortion Schemes: The new standard is stealing your PHI first. Attackers demand a ransom to unlock your systems and a second payment to prevent them from selling or publicly releasing the stolen data. This guarantees a HIPAA violation regardless of whether you pay.
Supply Chain Attacks
Attacks on third-party vendors are responsible for some of the biggest recent breaches, turning trusted partners into the biggest risks.
- Compromised Medical Devices: IoMT devices (like connected diagnostic equipment) with weak embedded security can be hijacked, not only to disrupt care but to use the device itself as a gateway to access an entire network or patient database.
- Third-Party Vendor Breaches: If a cloud EMR provider, billing service, or other business associate is breached, patient data is compromised, and the healthcare organization bears the HIPAA liability.
AI-Powered Attacks
The latest development is the weaponization of artificial intelligence by malicious actors.
- Deepfake Technology: Cybercriminals can now use deepfake audio to perfectly clone the voice of your security officer or an executive. They call an employee, sound exactly like a trusted authority, and issue a fraudulent, urgent instruction to bypass security protocols.
- Automated Vulnerability Scanning: AI tools can scan vast client networks for exposed medical devices at superhuman speeds, identifying and preparing attacks on thousands of targets simultaneously.
- Phishing Targeting Healthcare Workers: Attackers use generative AI to create highly personalized, context-aware phishing and spear-phishing emails that perfectly mimic the tone, jargon, and urgency of a vendor, an executive, or even a colleague.
- Business Email Compromise (BEC): This involves tricking staff into wiring money or releasing sensitive information by impersonating a CEO or senior manager.
Solutions for Cybersecurity in the Healthcare Industry

Protecting patient data in the mobile healthcare environment requires a multi-layered approach based on the HIPAA security rules discussed above. This Cybersecurity Awareness Month, focus on these essential safeguards to fortify your practice!
Technical Safeguards
MFA
This is your most critical defense against compromised credentials. Require a second form of verification (like a code from an app or a fingerprint) in addition to a password for every system, especially those containing ePHI.
End-to-End Encryption
All PHI must be encrypted, whether it is actively being sent across a network or simply stored on a device or server. If a device is lost (or a server is breached), encryption guarantees the data is unreadable.
MDM Solutions
MDM allows your practice to centrally manage, track, and secure all company- and employee-owned devices. Crucially, MDM enables remote-wipe capability to instantly erase all PHI if a device is lost or stolen.
Regular Software Updates and Patch Management
Treat every connected device, from laptops to IoMT, like a security priority. Apply operating system patches and software updates immediately to close known vulnerabilities that attackers frequently exploit.
Network Segmentation and Firewalls
Isolate the part of your network that holds ePHI from the rest. Firewalls restrict unauthorized traffic, and network segmentation prevents a breach in one area (like a guest Wi-Fi) from spreading to your critical patient data systems.
Administrative Controls
Holistic Cybersecurity Policies
Document everything. Create clear, mandatory policies on acceptable use, email handling, password strength, and when and how to report a security incident.
Regular Risk Assessments
HIPAA requires an annual, thorough evaluation of all potential threats and vulnerabilities to your ePHI. This assessment is the blueprint for your security spending, helping you prioritize where to allocate limited resources.
Incident Response Plans
Don't wait until a crisis hits! A written incident response plan (IRP) dictates the exact steps staff must take immediately following a breach (who to call, how to contain the threat, and when to notify authorities).
Business Continuity Planning
Keep your practice running even if systems are down. It is a good idea to have offline backups of your critical data so you can quickly restore services after a ransomware attack.
Physical Security Measures
Secure Storage of Mobile Devices
When not in use, all laptops, tablets, and mobile medical bags must be secured in a locked drawer, cabinet, or vehicle compartment. This mitigates the risk of theft when staff are on the road or off-site.
Clean Desk Policies
Staff must be trained never to leave paper documents, sticky notes with passwords, or devices unattended and unsecured. At the end of the day, all PHI must be locked away.
Visitor Access Controls
In any facility where PHI is accessible, all visitors, vendors, and non-essential personnel must be logged in and escorted while on the premises.
Building a Culture of Cybersecurity Awareness
To grasp the full importance of cybersecurity in healthcare, remember that technology and policies are just tools. When push comes to shove, your employees are your most valuable asset and your first line of defense.
Employee Training Programs
Effective training is a lot more than a one-time annual meeting. Instead, it's an ongoing, interactive process designed to keep security top-of-mind.
- Regular Cybersecurity Awareness Sessions: Conduct mandatory, frequent, and relevant training. These sessions should focus on the specific risks faced by staff, such as connecting to unsecured Wi-Fi or securely managing devices in transit.
- Simulated Phishing Exercises: Practice makes perfect, for both defense and offense. Running simulated phishing exercises allows you to test your employees' ability to spot a malicious email in a safe environment. Use the results to target training for those who click suspicious links, turning a vulnerability into a teaching opportunity.
- HIPAA Compliance Training: Ensure all staff understand what PHI is and their personal responsibility in preventing unauthorized disclosures.
Continuous Improvement
The threat landscape changes daily, which means your security strategy must evolve just as quickly.
- Regular Security Assessments: Beyond the annual HIPAA-mandated risk assessment, conduct routine internal audits and technical scans to find and patch vulnerabilities before a hacker does. The goal is to identify new risks introduced by updated software, new devices, or changes in staff roles.
- Staying Updated on Emerging Threats: Make it a priority to follow official warnings from the HHS and industry security groups. Be aware of the latest ransomware tactics so you can rapidly train your team on how to recognize them.
- Learning from Industry Incidents: Review details of data breaches at other healthcare organizations. Analyze how they were exploited and determine what changes your practice needs to make to avoid the same mistake. Every industry incident is a valuable, free lesson in prevention.
Practical Steps for Mobile Medical Services
Phase 1: Immediate Action (The Next 30 Days)
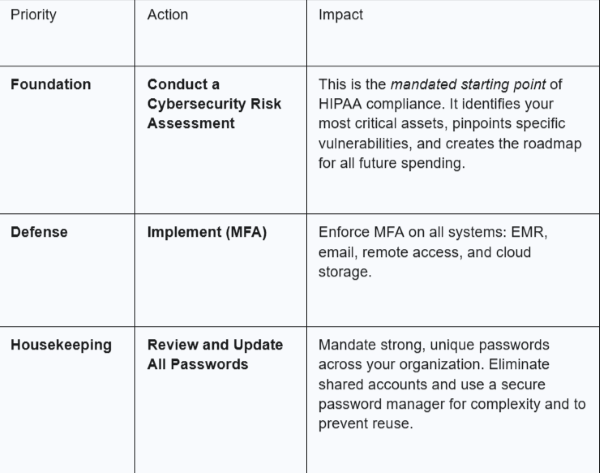
Phase 2: Short-Term Goals (The Next 90 Days)
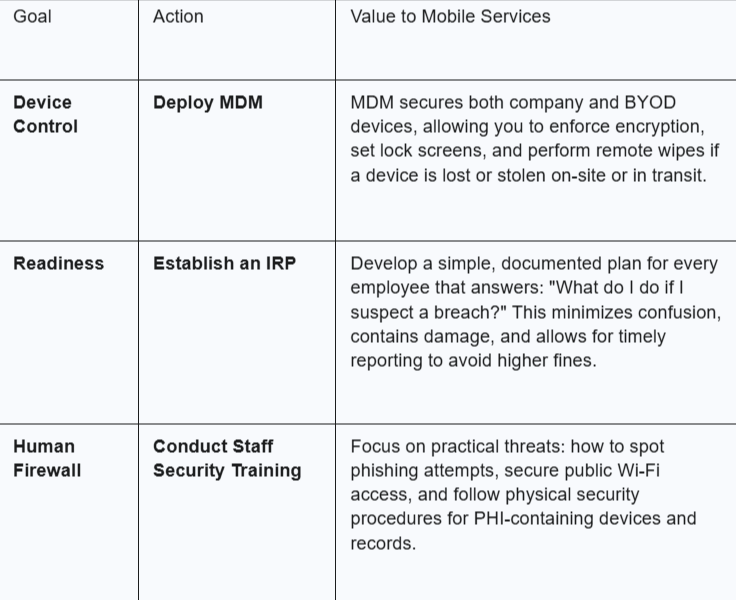
Phase 3: Long-Term Strategy (6–12 Months)
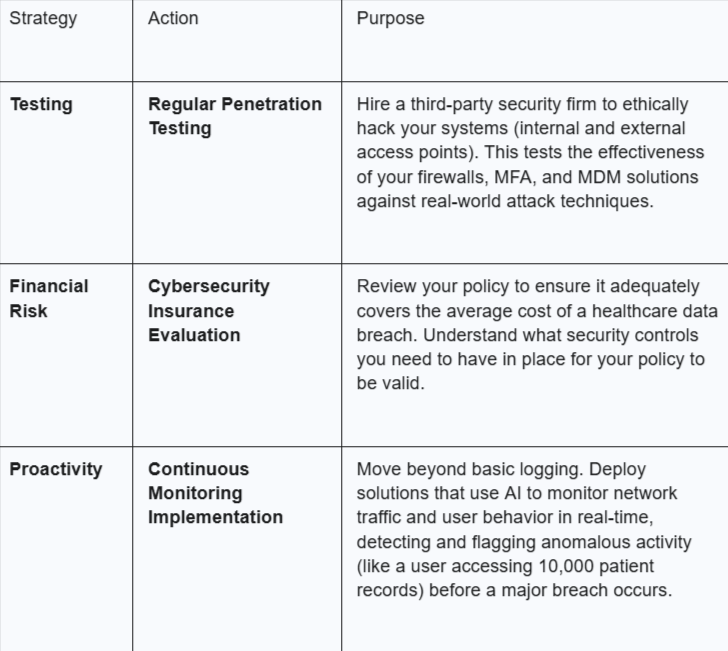
Mobile Medical Corporation: A Commitment to Secure Care
At Mobile Medical Corporation, we put cybersecurity first. We understand that the threat landscape is constantly advancing, which is why we are committed to always moving forward. We will continue to better our defenses against cybercriminals, staying one step ahead through proactive security improvements.
Contact us to learn more about how we are fortifying our services to safeguard patient data!




